
A policy is a condition or instruction that oversees IT operations or processes. It can be a rule that dictates which conditions must be fulfilled for a code in order to pass a security control and be deployed.
In this blog, you will learn:
- What is Policy as a Code
- What is OPA
- How to Get Started with Open Policy Agent?
- How to Download OPA on Linux?
- Rego Playground use Cases
- How to Use OPA With Terraform?
What is Policy as a Code
Using code to design and manage rules and conditions is known as policy-as-code. Under a policy-as-code approach, teams write out policies using some type of programming language, similar to Python, YAML, or Rego. The specific language generally depends on which policy-as-code management and enforcement tools you are using.
What is OPA
The Open Policy Agent, also known as OPA, is an open-source, general-purpose policy engine that can be used to enforce policies in Terraform, Kubernetes, microservices, and many more. It uses a policy language called Rego, which allows you to write policies declaratively as code and then use them as a part of the decision-making process.
OPA was developed by Styra and is currently a part of CNCF (Cloud Native Computing Foundation). Netflix is one of the examples that employ OPA to manage access to internal API services.
OPA can be used for a variety of things, such as:
- Authorization of REST API endpoints.
- Allowing or denying Terraform changes based on compliance or safety rules.
- Integrating custom authorization logic into applications.
- Enforcing Kubernetes Admission Controllers to validate API requests.
Policies can be written as code using Rego. Rego prefers the policy to be human-readable and was inspired by Datalog. It also has a very simple syntax. OPA takes input data as JSON and checks the Rego policies against it. Because OPA and Rego are domain-agnostic, you may use them to specify nearly any type of invariant in your policies, such as below,
- Who has access to which resources?
- Which subnets are allowed to receive egress traffic?
- The clusters to which a workload must be deployed.
- From which registries may binaries be downloaded?
- The capabilities of the operating system on which a container can run.
- At what times of the day may the system be accessible?
How to download OPA on Linux?
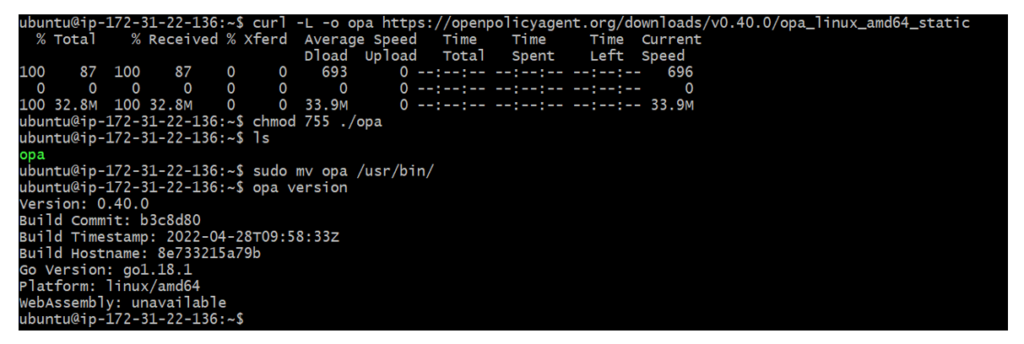
Follow the below steps to download and install OPA on Linux,
Step1: Run the below command to download OPA.
$ curl -L -o opa https://openpolicyagent.org/downloads/v0.40.0/opa_linux_amd64_static
Step2: Set permissions on the OPA executable.
$ chmod 755 ./opa
Step3: Move the executable to /usr/bin in order to run opa anywhere.
$ sudo mv opa /usr/bin/
Step4: Check the version to validate everything is set up correctly.
$ opa version
Refer to the below screenshot which shows all of the above commands,
- Data: It is a collection of facts about the world that OPA considers when making a choice.
- Input: The computation of a decision is triggered by the input. It specifies the issue that OPA should resolve. The query input must be JSON structured.
- Policy: For the given data and query input, Policy defines the computational logic that produces a policy decision, also known as a query result.
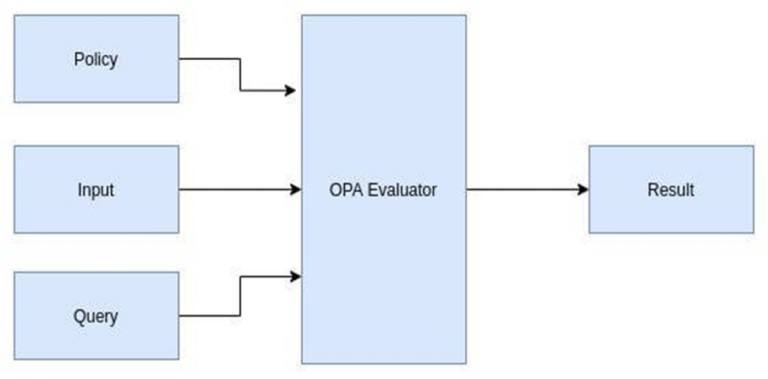
OPA takes a policy, input, and query; and creates a response depending on these. Input can be any valid JSON document, which allows OPA to be integrated with any tool that generates JSON output.
Rego playground use cases
The playground helps you to try out new policies and learn the language quickly.
Trying Rego Playground: Your first code
The fastest way to try out OPA is “Rego Playground”.
For a demo of the Rego Playground and some of its features check out the picture below. You can see sections for writing your Rego code, adding Input, and then in the bottom right section, you can see the Output.
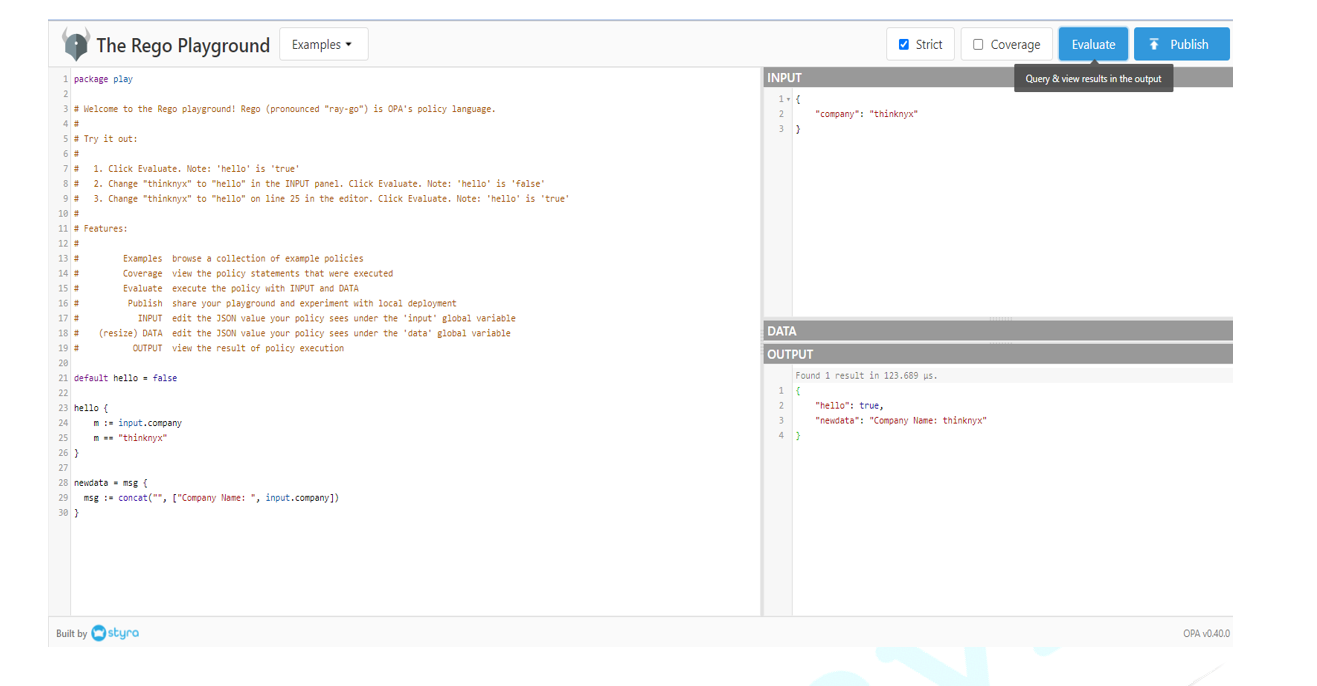
Add the below lines to the left pane. These are sample inputs that we are passing to test our code.
newdata = msg {
msg := concat(“”, [“Company Name: “, input.company])
}
Click Evaluate button located on the top right of the playground.
To explore the playground, you may visit The Rego Playground.
Now that we have explored the basics, let’s see how to use it with Terraform.
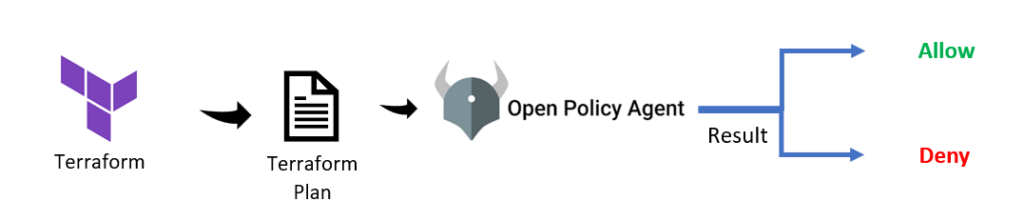
How to Use OPA With Terraform?
Terraform can generate a plan in JSON format via the ‘terraform show -json’ command. This means we can outline policies for our infrastructure, and use OPA to decide whether a plan is safe to implement or not.
For example, we have the following Terraform definition to create an EC2 instance:
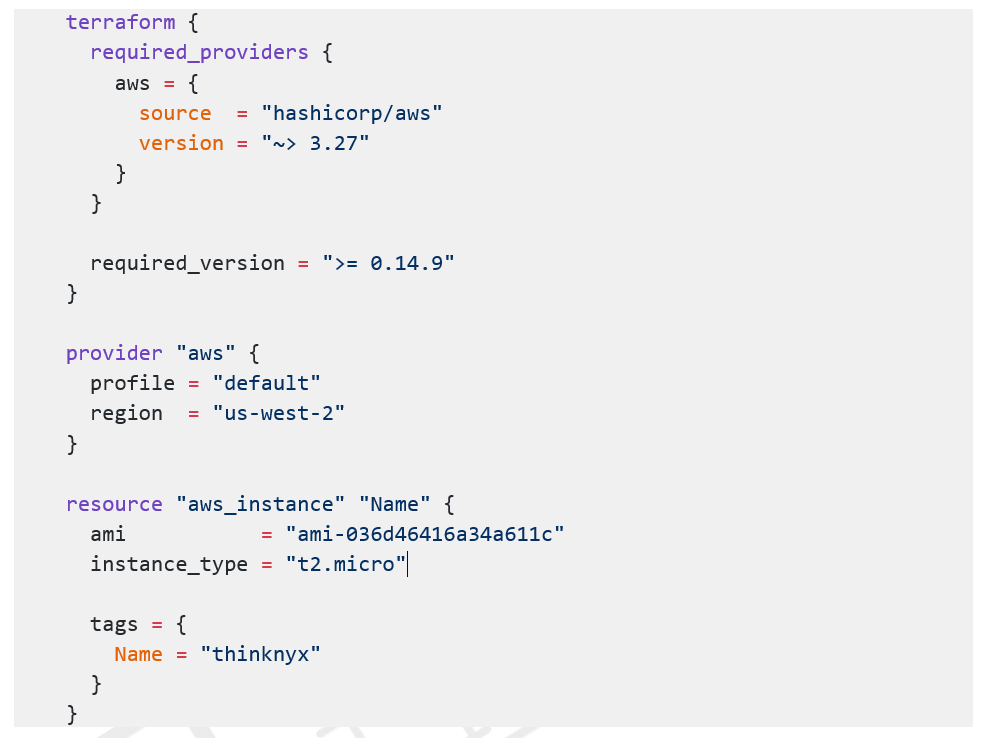
Now, we want to ensure that every Terraform resource has a ‘Name’ tag. We could enforce that by creating a file called ‘tag.rego’ with the following code:
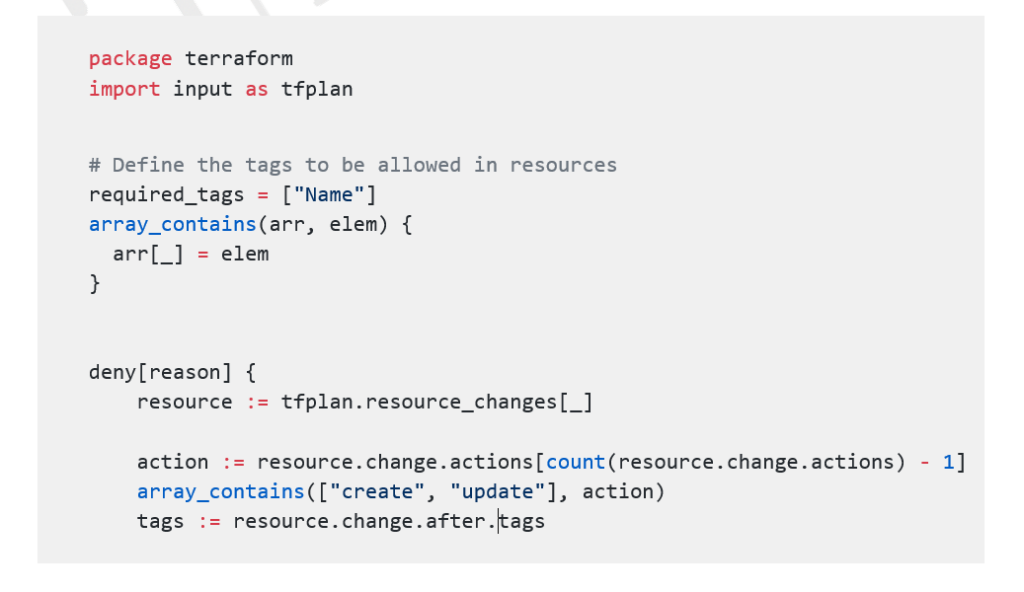
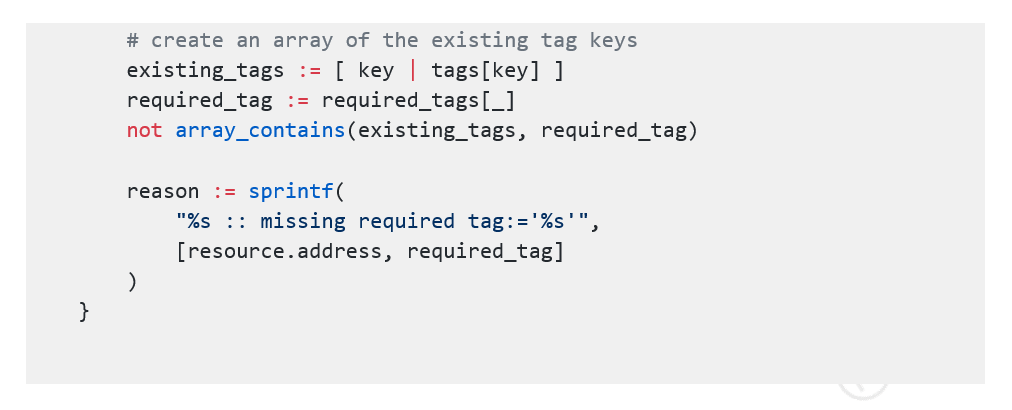
For this, we need to perform the following steps:
- Generate a Terraform plan as a JSON file.
- Run ‘opa eval’ to verify if that plan passes our policy.
Step 1 – Generate our Terraform plan as JSON
To get a JSON representation of our plan, we must first save it to a file and then use the ‘terraform show -json’ command to generate that plan in JSON format.
$ terraform plan –out thinknyx_ec2
$ terraform show -json thinknyx_ec2 > thinknyx_ec2.json
- As ‘thinknyx.json’ file is too long, we are showing some parts of json below:
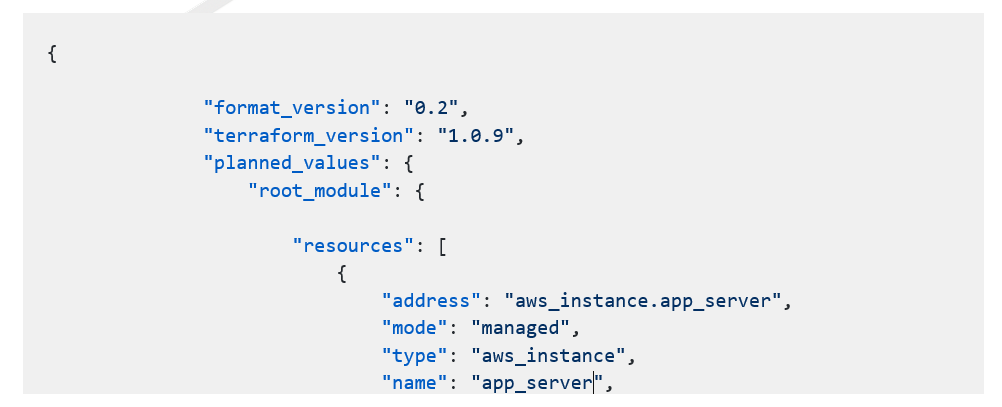
Step 2 – Run ‘opa eval’
Now we will use ‘opa eval’ to evaluate the plan against our policy:
- If the policy allows the terraform plan after running the below command, we will get the below output:
$ opa eval –format pretty –data tag.rego -i thinknyx.json data.terraform.deny
Output:
[ ]
- If the policy denies the terraform plan after running the below command, we will get the below output:
$ opa eval –format pretty –data tag.rego -i thinknyx.json data.terraform.deny
Output:
[
“aws_instance.app_server :: missing required tag:=’Name’”
]
Conclusion
Now, that you have some fundamental knowledge about OPA, I hope you’ve found this blog educative and it has helped you to understand the role of OPA, how to use Rego to create custom templates, and how it works with its input so that you may create your own policies and get the most out of OPA.
References
OPA documentation – It is a great resource for learning Rego as well as creating or reviewing the policy. Many popular OPA applications, including Kubernetes, Terraform, and others, are covered in the documentation.
Introduction to OPA || Open Policy Agent
This video will provide you the fundamental knowledge on OPA, why it is used and how does it work.