Hacking Explained: A Guide for Newcomers
In this blog, we will delve into the fundamentals of hacking, the cyber kill chain methodology, the tactics, techniques, and procedures (TTPs) employed in hacking, and hacking class. This content is designed for absolute beginners aspiring to embark on a career in ethical hacking.
What is Hacking?
Hacking is often defined as the act of compromising digital devices and networks by gaining unauthorized access to accounts or computer systems. While hacking isn’t always driven by malicious intent, it’s typically linked with illegal activities and data theft carried out by cybercriminals.
There are mainly two types of hacking. First one is Ethical, and another one is Unethical hacking.
Unethical Hacking
Unethical hacking is a term used to describe the unauthorized access, exploration, and manipulation of computer systems, networks, and data. It involves exploiting vulnerabilities in software, hardware, or human factors to gain access to information that is otherwise protected.
Hackers, the individuals or groups who engage in hacking activities, often have different motives. Some hackers seek to steal sensitive information, such as personal data or financial records, for personal gain or to sell on the black market. Others may hack systems to disrupt operations, cause damage, or spread malware.
Ethical Hacking
Ethical hacking, also known as penetration testing or white hat hacking, is the practice of testing computer systems, networks, or applications for security vulnerabilities that could be exploited by malicious hackers. Ethical hackers use their skills and knowledge of hacking techniques to identify and report vulnerabilities to the system owners so that they can be fixed before they are exploited by cybercriminals. Ethical hacking is conducted with the permission of the organization that owns the system being tested. The goal is to uncover potential security weaknesses and help the organization improve its security posture. Ethical hackers use the same techniques as malicious hackers, such as scanning for open ports, exploiting known vulnerabilities, and conducting phishing attacks, but they do so with the intent of improving security rather than causing harm.
Ethical hacking is an important practice for organizations looking to protect their systems and data from cyber threats. By proactively identifying and fixing vulnerabilities, organizations can reduce the risk of a security breach and protect sensitive information from being compromised.
Tactics, Techniques, and Procedures (TTPs)
Tactics, Techniques, and Procedures (TTPs) are concepts used in cybersecurity and intelligence analysis to describe the methods used by threat actors to achieve their objectives. Here’s a breakdown of each component:
- Tactics: Tactics refer to the overarching goals or objectives of a threat actor. They represent the high-level strategic decisions made by the attacker to achieve their ultimate goal. For example, a tactic might be to gain unauthorized access to a network or to steal sensitive information.
- Techniques: Techniques are the specific methods or actions used by threat actors to accomplish their tactical objectives. These are the actual steps taken by the attacker to exploit vulnerabilities, gain access to systems, or perform malicious activities. Techniques can include using malware, social engineering, exploiting software vulnerabilities, and more.
- Procedures: Procedures are the detailed, step-by-step instructions followed by threat actors to execute their techniques. Procedures are often specific to the tools and infrastructure used by the attacker and can include commands, scripts, configurations, and other actions taken to carry out an attack.
Understanding the Tactics, Techniques, and Procedures used by threat actors is critical for effective cybersecurity defence. By recognizing the patterns and behaviours associated with different TTPs, organizations can better detect, prevent, and respond to cyber threats.
Hacker class
- Black Hat: A black hat hacker exploits computer systems with malicious intent, engaging in illegal activities like data theft, malware distribution, and DDoS attacks. Their actions contrast with ethical hackers, as they prioritize personal gain or disruption over security.
- White Hat: A white hat hacker ethically tests and secures computer systems by identifying and fixing vulnerabilities. They work to protect against cyber threats, ensuring system safety and compliance with security standards.
- Grey Hat: A grey hat hacker exploits computer systems without malicious intent, often acting without permission to identify vulnerabilities. They may disclose these issues to the system owners or the public, operating in a legal and ethical way.
- Script Kiddies: Script kiddies are amateur hackers who use pre-written scripts or tools created by others to exploit computer systems, lacking advanced technical skills or deep understanding. Their actions are often driven by a desire for attention or mischief rather than malicious intent.
Cyber Kill Chain Methodology
The Cyber Kill Chain methodology plays a crucial role in intelligence-driven defence, aiding in the detection and prevention of malicious intrusion activities. By outlining the steps that adversaries typically follow to achieve their objectives, this framework assists security professionals in understanding and mitigating cyber threats effectively.
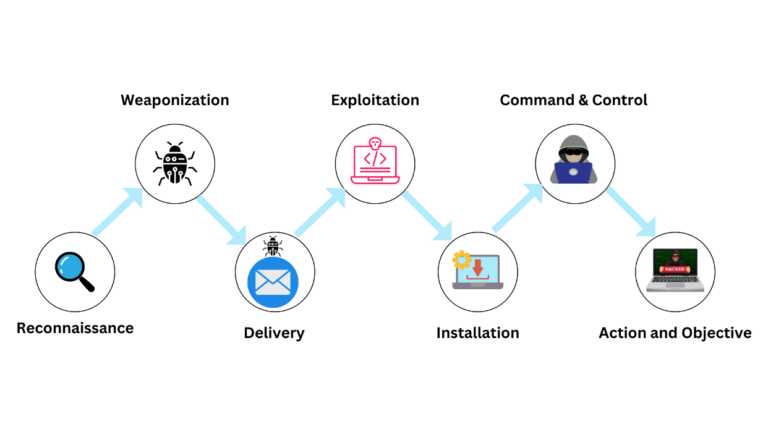
Inspired by military kill chains, the Cyber Kill Chain provides a structured approach to securing cyberspace, focusing on enhancing intrusion detection and response capabilities. With its seven-phase protection mechanism, the Cyber Kill Chain enables organizations to proactively mitigate and reduce cyber threats. Various phases included in it are:
- Reconnaissance: Reconnaissance is the initial stage of an attack where the attacker gathers information about the target. This information can include identifying potential vulnerabilities, understanding the target’s infrastructure, and gathering information about key personnel. Reconnaissance is typically conducted using passive techniques, such as scanning public websites and social media profiles, to gather information without directly interacting with the target’s systems. The goal of reconnaissance is to gather enough information to plan and launch a successful attack against the target.
- Weaponization: Weaponization refers to the stage where an attacker creates or acquires a malicious payload that can be used to exploit vulnerabilities in the target’s systems. This payload could take various forms, such as malware, viruses, or phishing emails, and is designed to deliver the attacker’s malicious intent. The goal of weaponization is to prepare the malicious payload for delivery to the target, where it will be executed to exploit vulnerabilities and gain access to the target’s systems or data.
- Delivery: Delivery is the stage where the attacker delivers a malicious payload to the target’s systems or network. Delivery can occur through various means, including email attachments, malicious links in emails or on websites, USB drives, or even physical access to a system. The goal of the Delivery stage is to get the malicious payload onto the target system so that the attacker can proceed to the next stages of the Cyber Kill Chain, such as exploitation and installation, to achieve their objectives.
- Exploitation: Exploitation refers to the stage where the attacker takes advantage of a vulnerability to gain access to a target system or network. This vulnerability could be a software bug, misconfiguration, or a weakness in the system’s defences. Once the attacker exploits the vulnerability, they can gain a foothold in the target environment and proceed with their attack. Exploitation often involves using malicious code or techniques to gain unauthorized access, such as executing a remote code execution exploit or leveraging a phishing attack to trick a user into revealing sensitive information.
- Installation: The stage where the attacker installs additional tools or malware on the compromised system to maintain access and gather information. Once the initial exploitation of vulnerabilities has occurred, the attacker may deploy various malicious software to establish persistence and further their objectives within the target environment. This could include installing keyloggers, remote access Trojans (RATs), or other types of malwares that allow them to control the compromised system remotely and continue their attack.
- Command & Control: Command and Control (C2) in the Cyber Kill Chain is when attackers establish communication with compromised systems to control them. Defenders must detect and disrupt this phase to prevent attackers from carrying out their objectives.
- Actions and Objectives: It is the final stage of a cyberattack where the attacker achieves their ultimate goal. This stage can vary depending on the attacker’s objectives, like Data Exfiltration, Data Destruction, System Disruption, Espionage, Financial Gain, and Reconnaissance. Actions on Objectives represent the culmination of the attacker’s efforts and the realization of their goals. Understanding the potential objectives of an attacker can help organizations better defend against cyber threats by implementing appropriate security measures and controls.
Consider a scenario in which an attacker identifies a target financial institution, XYZ Bank. The attacker gathers information about the bank’s employees through LinkedIn, social media, and the company’s website. They focus on employees in the finance and IT departments. The attacker crafts a spear-phishing email using the gathered information. The email contains a malicious PDF attachment that appears to be an internal financial report. The PDF file is embedded with a remote access Trojan (RAT). The attacker sends the spear-phishing email to several employees at XYZ Bank. The email appears to come from the bank’s internal finance team, making it more likely for the recipients to open it. An employee in the finance department opens the malicious PDF attachment. The embedded RAT exploits a vulnerability in the PDF reader software, allowing the attacker to execute code on the employee’s computer. The RAT installs itself on the employee’s computer, establishing a persistent backdoor for the attacker. The malware modifies the system’s startup routine to ensure it runs whenever the system boots. The RAT connects to the attacker’s C2 server over an encrypted channel. This allows the attacker to remotely control the infected machine without detection. The attacker uses the RAT to escalate privileges on the infected computer, gaining administrative access. They then move laterally within the network, accessing sensitive financial data and internal systems. The attacker exfiltrates this data to their own servers for later use or sale on the dark web.
Conclusion
Understanding the distinctions between ethical and unethical hacking is crucial for aspiring cybersecurity professionals. Ethical hackers safeguard systems by identifying vulnerabilities before malicious actors exploit them. The Cyber Kill Chain methodology and Tactics, Techniques, and Procedures (TTPs) provide valuable insights into attack strategies and defence mechanisms. Recognizing different hacker classes helps tailor defensive strategies. A career in ethical hacking is rewarding and impactful, contributing to a safer digital world through continuous learning and proactive security measures.
By – Kumar Kanishk